Snowflake Data Monitoring Policies Document
General Information
- TrustLogix supports the following policy definitions on the below principals and resources
- Principals : All, User, User IP, User Application
- Resources : Account, Database, Schema, Table, View, Privilege, Role
- Policy details
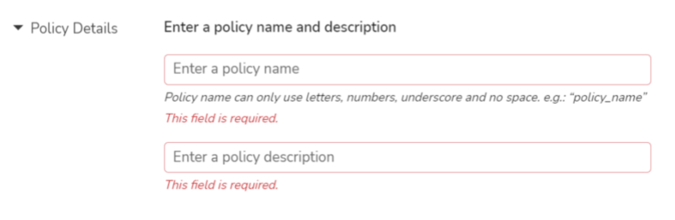
- Policy Name : Valid name for the policy without spaces in between
- Policy Description : description of what this policy is meant for
- Principal, condition and List type detail
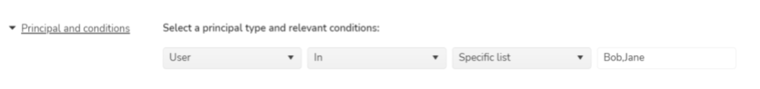
- Principal type : One of the values among User, User IP, User Application and All
- Choosing “All“ indicates it can be any user or IP or application
- Condition type : One of the values among In and Not In
- Note : Principal type “All“ has no condition type field to populate
- List type : One of the values among Whitelist and Specific List
- When Specific List is chosen as an option, user has to enter one or more values eg : Bob,Jane when principal type is User and the list type is Specific List
- For the Whitelist option refer to TrustLogix Classification and Whitelisting section at the bottom of this document.
- Principal type : One of the values among User, User IP, User Application and All
- Monitoring resource, classification and action details
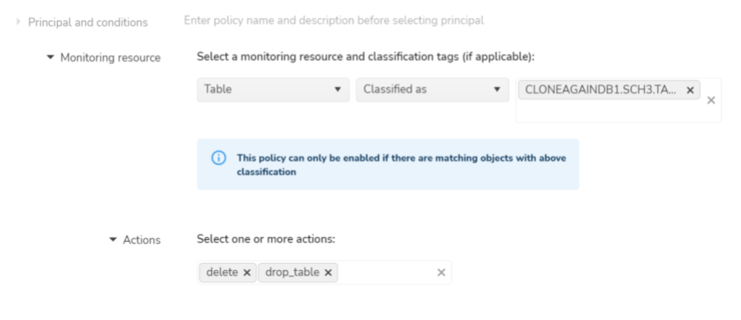
- Resource type : Varies based on the data source type
- Snowflake has the following resource types Account, Schema, Database, Table, View, Privilege and Role
- Classification type or Specific Names
- Note : Resource type “Account“ has no classification type or specific names field to populate
- Note : Resource types “Privilege“ and “Role“ have no classification types field to populate
- Classification information can come from the “Snowflake“ DB or they can be created within the TrustLogix classification page. Refer to TrustLogix Classification and Whitelisting section at the bottom of this document for classification within the TrustLogix product.
- Action type : The values are based on the resource type selected
- Eg : Resource type “table” will have actions such as “alter_table“, “clone_table“, “drop_table“ etc
- Resource type : Varies based on the data source type
- Alert frequency, severity, and category details
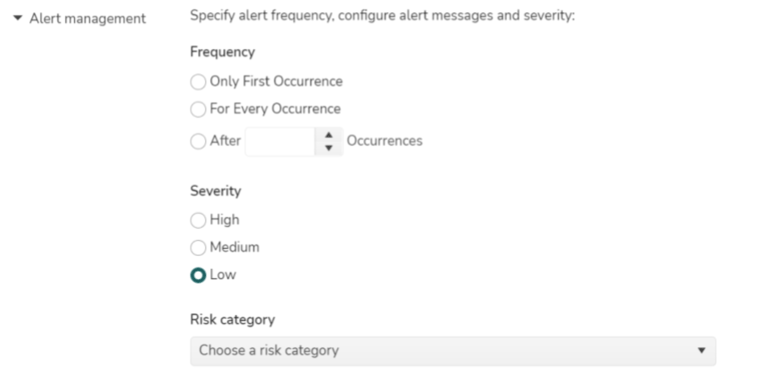
- Frequency type : One of the values among Only First Occurrence, For Every Occurrence and After N Occurrences
- Only First Occurrence will trigger an alert the first time the policy matches the ingested records
- For Every Occurrence will trigger an alert every time the policy matches the ingested records
- After N Occurrences will trigger an alert when the record count is greater than the N value provided
- Severity type : One of the values among High, Medium and Low
- This value has to be set based on the business criticality of the alert triggered by this policy
- Risk category type : One of the values among Dark Data, Shadow IT, Overly Granted Access, Security Misconfigurations, Data Exfiltration and Regulatory Compliance
- Dark Data : This category is set for data that is present but not accessed over a period of time
- Shadow IT : This category is set for users, applications and IP addresses that are not whitelisted or sanctioned to access the data source
- Overly Granted Access : This category is set for users who are granted excessive permissions or privileges within the data sources
- Security Misconfigurations : This category is set for data sources which have misconfigurations in terms of security
- Data Exfiltration : This category is set for actions that are primarily used to copy or clone data from the data source being monitored
- Regulatory Compliance : This category is set for data sources which do not have proper compliance standards like IP whitelisting etc
- Frequency type : One of the values among Only First Occurrence, For Every Occurrence and After N Occurrences
- Alert text, recommendation and status details
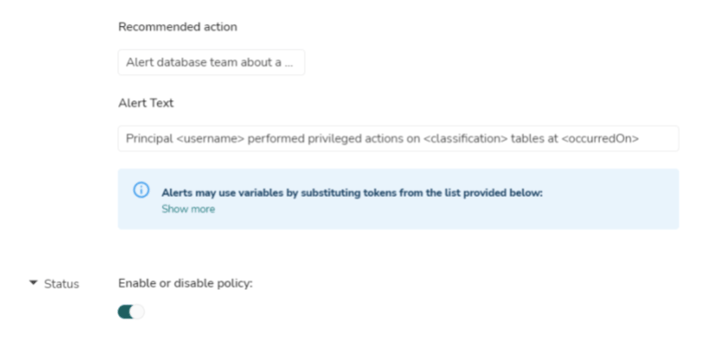
- Alert text : This field is used to populate the alert message that will be shown on the “Risk Activities“ page within TrustLogix console
- The following keys can be used to build the alert text message

- eg : User <username> performed privileged actions on tables classified as <classification> at <occurredOn>
- The following keys can be used to build the alert text message
- Recommendation : This field is used to populate the remediation or recommendation message for the corresponding alert
- eg : Notify information security officer that a non white listed user performed privilege actions on classified tables
- Status : This field is used to enable or disable the monitoring policy
- Note : policies using classification will not take effect unless the resources are classified appropriately.
- eg : Tables classified as PII policy will not take effect unless the appropriate tables in the data sources are tagged as PII
- Alert text : This field is used to populate the alert message that will be shown on the “Risk Activities“ page within TrustLogix console
TrustLogix Classification and Whitelisting
- Classification details
- There are two ways to add classifications to various resources with in a data source. One way is to add it within Snowflake DB and another way is to add it within TrustLogix UI
- This section will showcase on how to add various classifications within TrustLogix UI
- Click on the ellipsis as shown in the image above. This will open up the below popup.
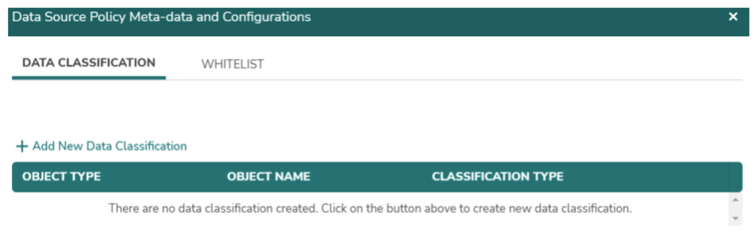
- Clicking on the “+ Add New Data Classification“ link will allow to add classification tags like Pii, Sensitive etc. to different object types such as Table, View etc
- Whitelist details
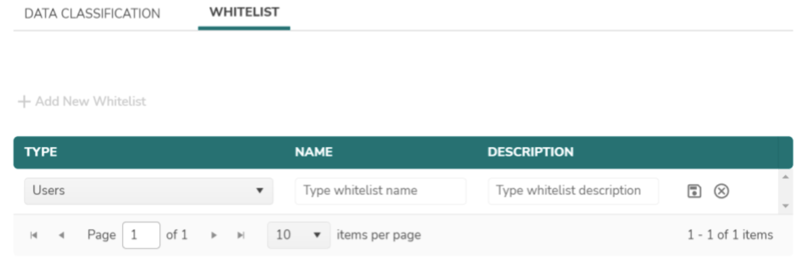
- Similar to the above data classification, whitelist can be added in a similar manner.
- Currently three types of whitelisting are supported.
- Users eg : Bob
- Applications eg : Tableau
- IP Address eg : 10.0.0.8 (single IP) or 10.0.0.8-10.0.018 (start and end IP range)
- NOTE : If there are multiple users, then each user has to be added as a line item in the whitelist UI page. This is also applicable to applications and IP addresses.
